Mate, your smart lightbulb is tracking your location
Answering a friends question on why his lightbulb app was asking for location permissions. An archive of the "live tweeting" which lead to the answer ...

12:25 PM · Jul 5, 2023
A friend asked me to find out why his connected lightbulb app was asking for his location, so I ducked out to Australia’s favourite hardware store, Bunnings, and grabbed one to check out.
The Android grid connect app has 500k+ downloads.
12:53 PM · Jul 5, 2023
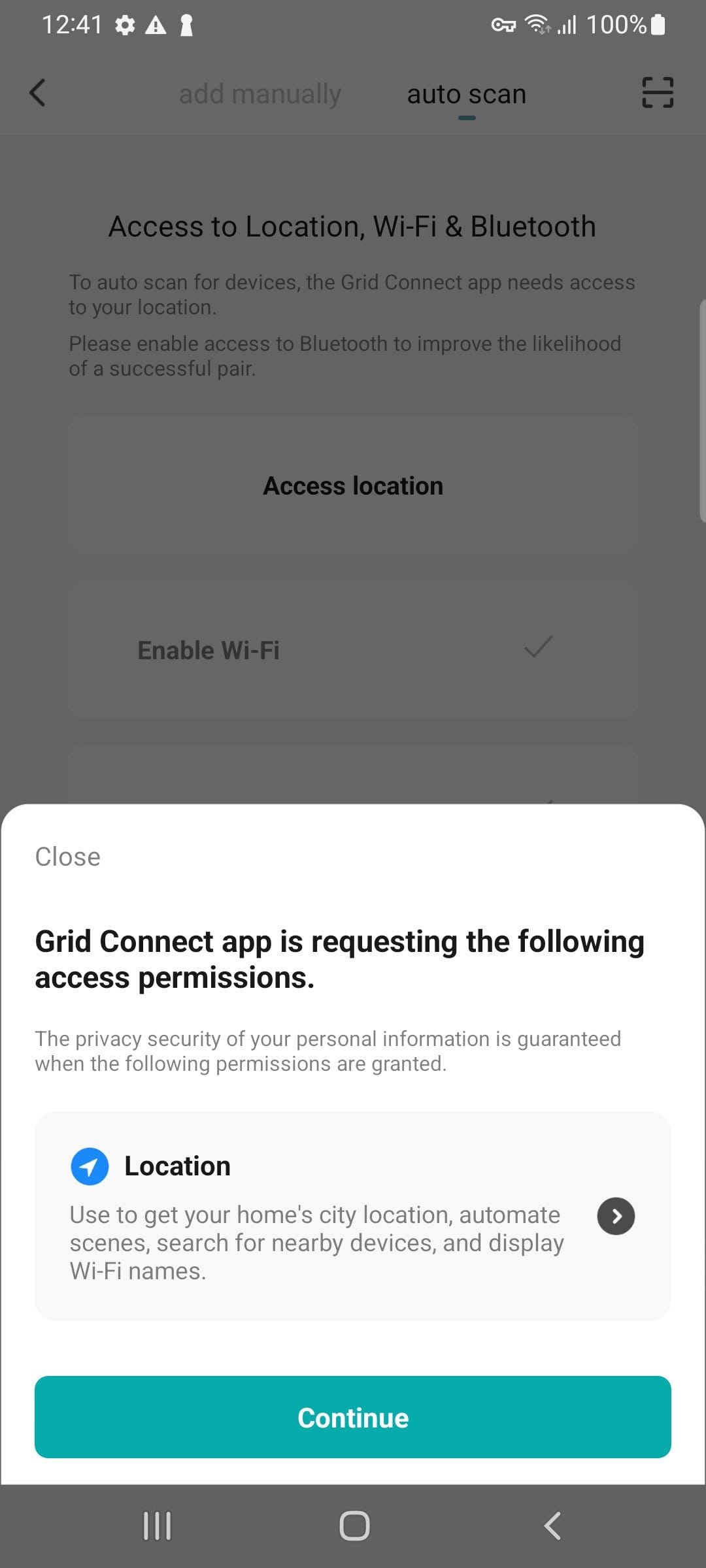
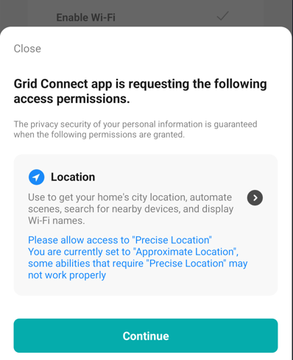
The app has a feature where it can auto discover your BLE devices. Is locations permission needed here? It depends. From Android API SDK v31 things have improved where fine location is not needed for BLE scanning.
The app is forcing this even though we are on v31.
1:01 PM · Jul 5, 2023
Let's allow it "for science". The device is paired. We also have the option to enter our Wifi credentials. I assume this is so the light can be remotely controlled over the Internet. It's automatable too. One condition is "when location changes". Let's not touch these.
1:08 PM · Jul 5, 2023
Time to fire up trusty #mitmproxy to look at the network traffic. Traffic is going to http://tuyaeu.com. Familiar domain. I came across Tuya used in a Mirabella Genio Smart light I got at a supermarket.
Tuya is an IoT OEM found everywhere.
postData is encrypted.
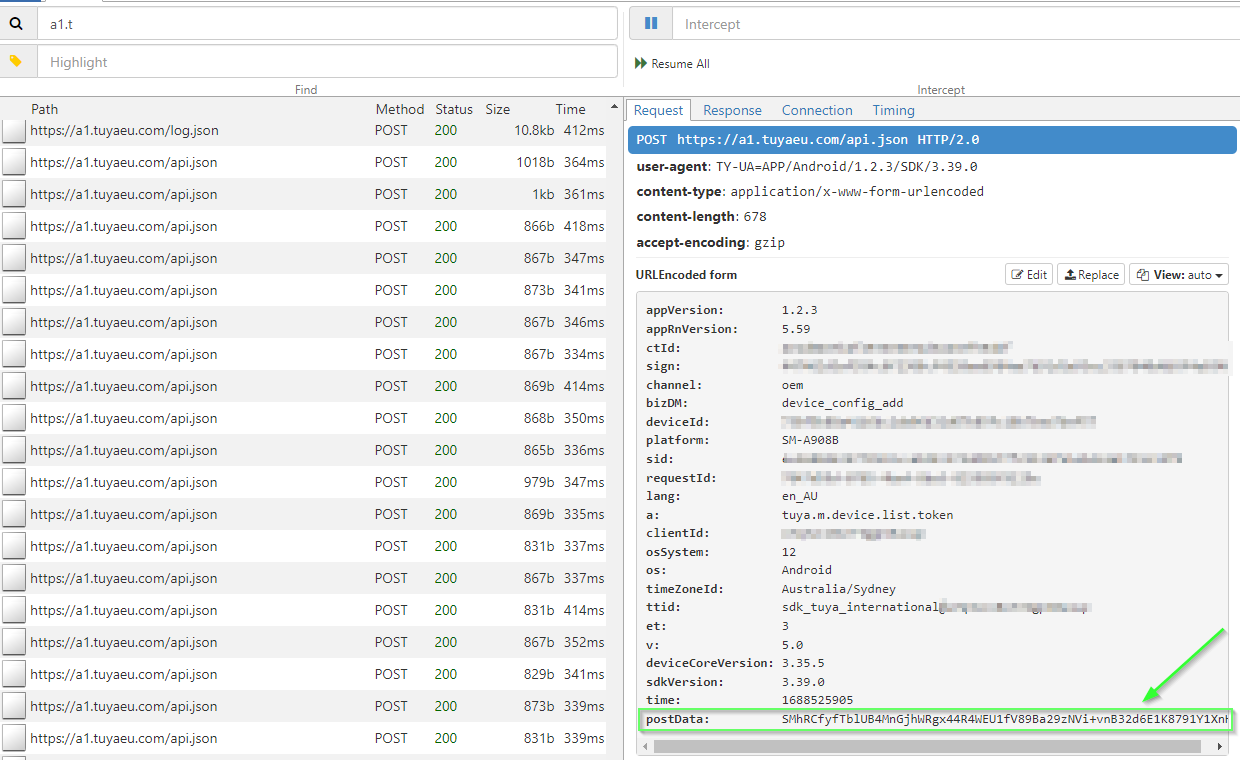
1:15 PM · Jul 5, 2023
Let's pull the .apk from the device and take a look at the manifest. We could of course grab it from APK Pure.
https://m.apkpure.com/grid-connect/com.arlec.gridconnect…
Yikes! recording audio, access to camera, location..
Assume there is a legitimate functional use for all of this. Trust but verify?
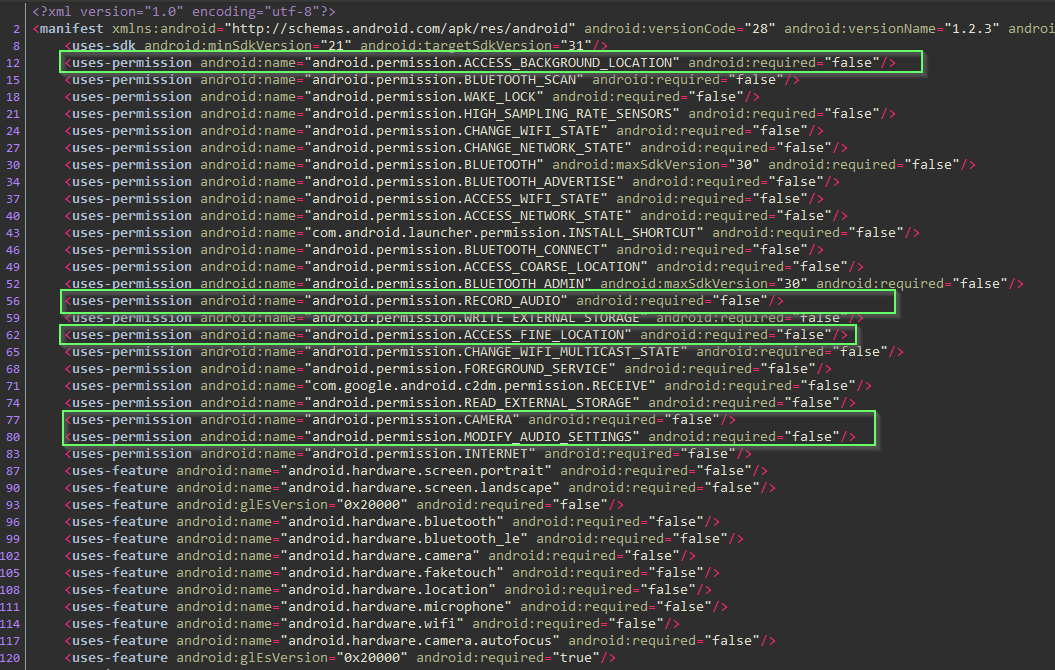
1:31 PM · Jul 5, 2023
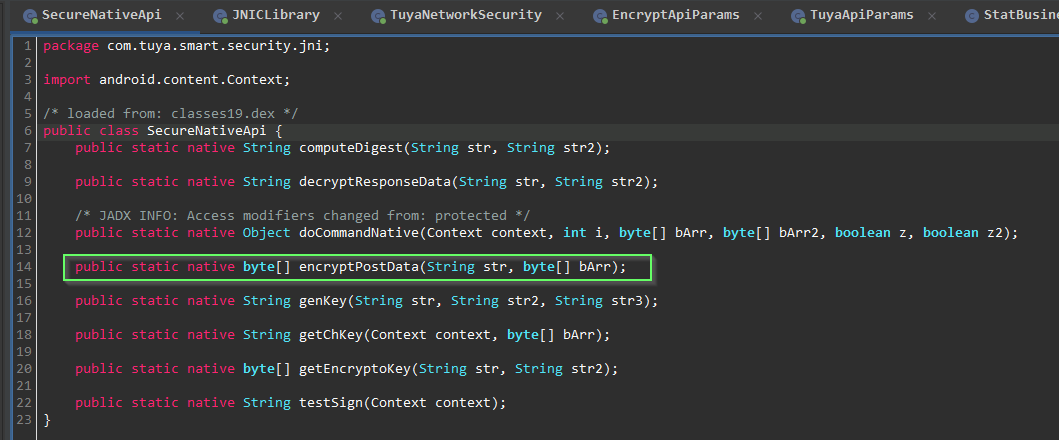
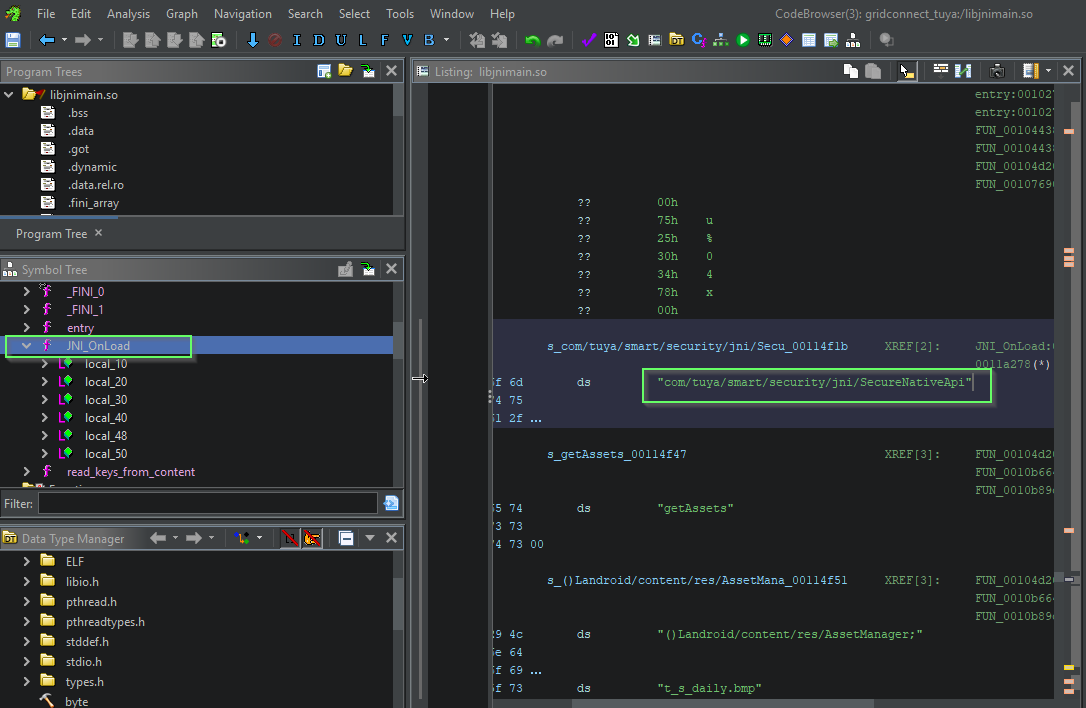
Our focus here is what is happening with location permission other then BLE scanning. We need quick wins as this app isn't trivial and is obfuscated. Crypto routines related to the postData appear to implemented in native arm64 within a shared library.
1:38 PM · Jul 5, 2023
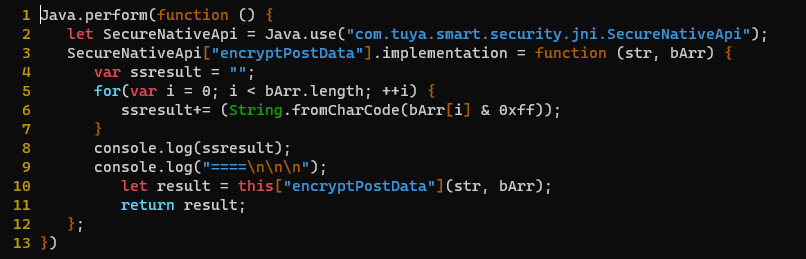
Dynamic instrumentation with #frida will really speed things up. JADX can emit a boiler plate hooking .js snippet to use in Frida. We just need to modify to to convert the plaintext byte array passed into encryptPostData from signed integers into a readable string.
1:48 PM · Jul 5, 2023
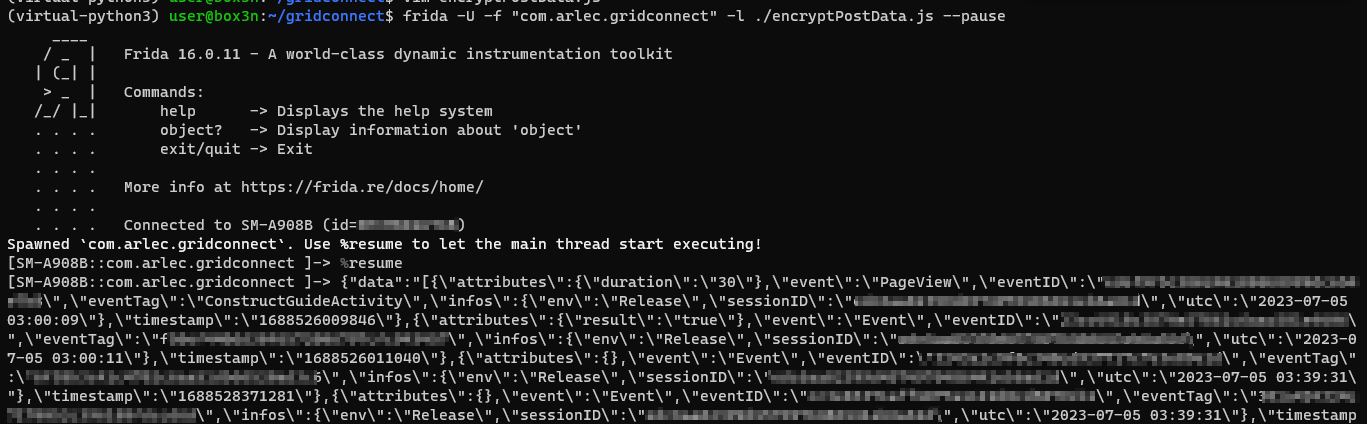
Looks like it worked! We have visibility on any data that is passed as a parameter to encryptPostData().
No need to reverse the encryption function to figure out how to decrypt the data - we have it before it's encrypted and sent over the wire.
MASSIVE TIME SAVER.
3:05 PM · Jul 5, 2023
So far no location data. Are we looking in the right place?
Remember we are after "quick wins". The minimum time investment possible to answer my friend's question "what's it doing with my location" ?
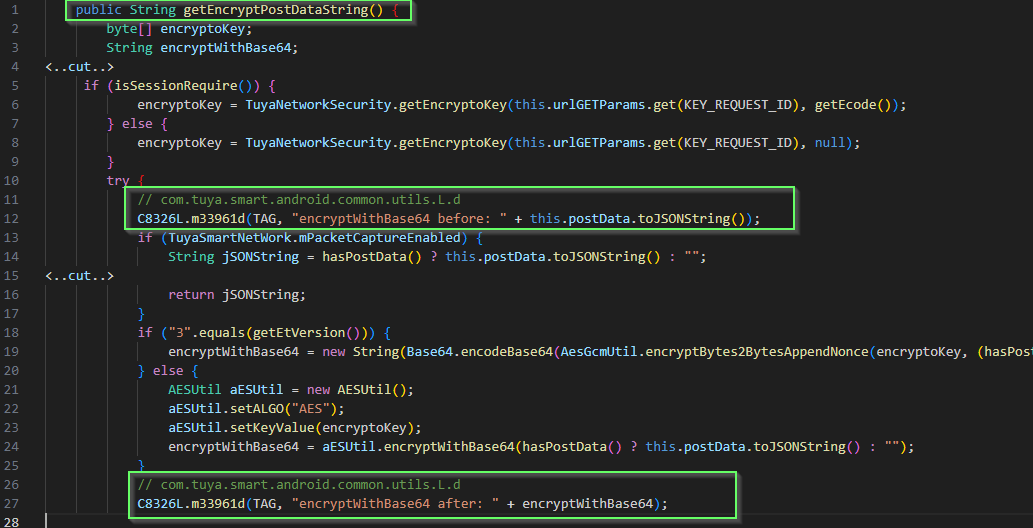
The developer's logging class seems perfect to hook into - getEncryptPostDataString() logs the encrypted data before and after.
We can then match the encrypted strings in appearing in the MITM'd HTTP post network traffic.
Perfect.
Let's ensure we include backtraces so we can get the function call flow which helps us navigate the decompilation.
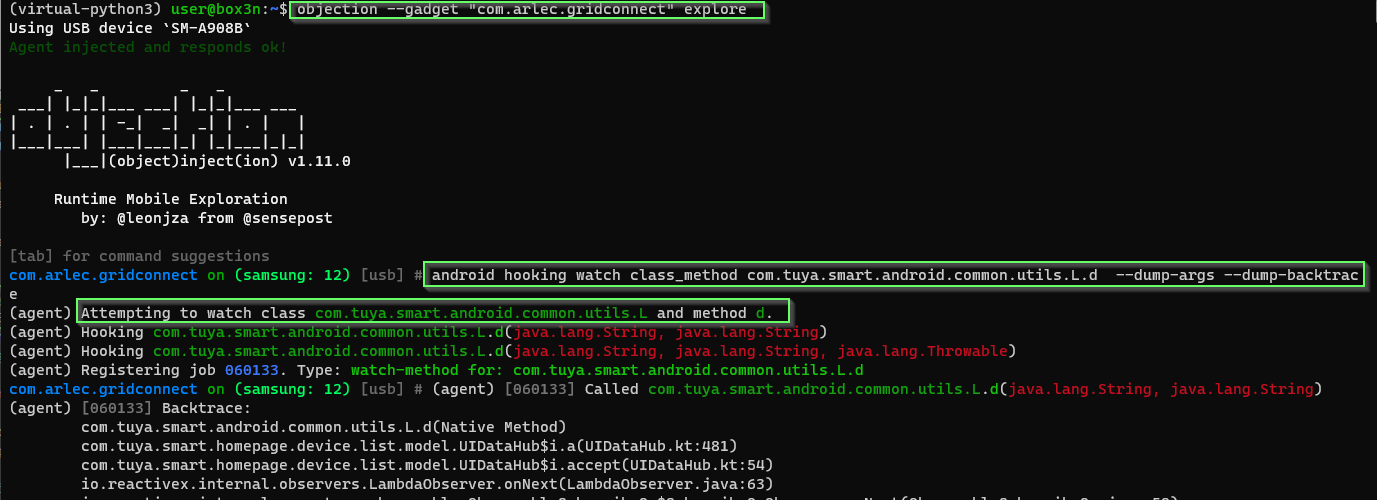
3:20 PM · Jul 5, 2023
You beauty - it worked. We now have visibility into what is encrypted in the postData form field.
We can account for the data in HTTP post towards the Tuya cloud API endpoint.
But what are we exactly looking for?
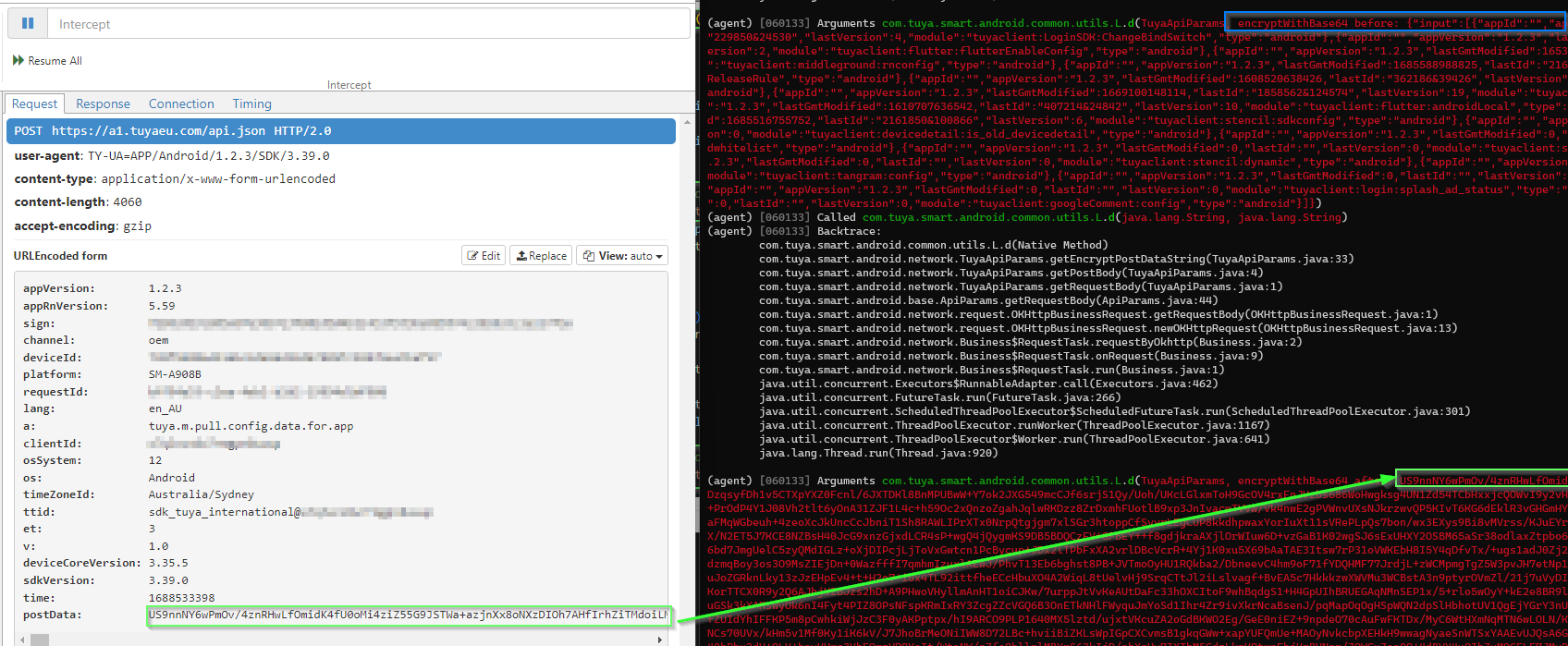
3:49 PM · Jul 5, 2023
Probably these parameters? "lat" and "lon".
hmm.. KEY_IMEI and KEY_IMSI are probably worth looking into too at some point.
But alas, we must stay on track. KEY_LAT and KEY_LON it is for now.
Live tweeting this enquiry keeping me on track
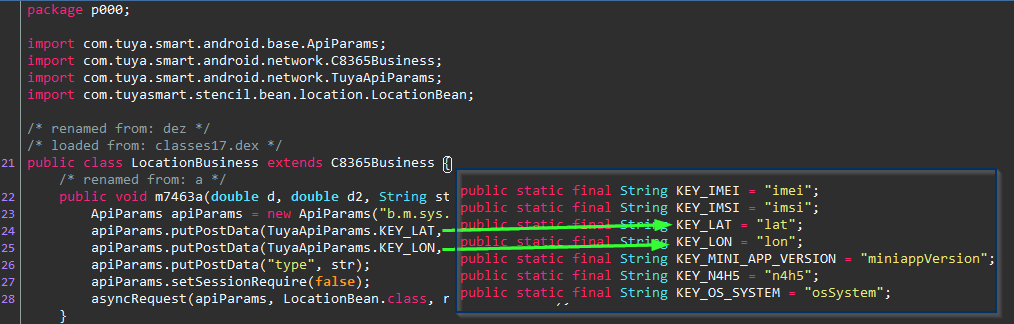
4:24 PM · Jul 5, 2023
ok, we got a match. GPS co-ordinates of where I am - although this was data *received* from the cloud server. How did my location get there in the first place? Perhaps when the application was first installed? Back to square one - but this time we know what to log.
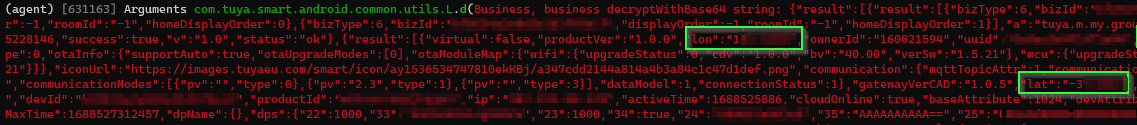
4:40 PM · Jul 5, 2023
Application reinstalled.
Boom! we see the exact packet where our GPS co-ordinates are sent to Tuya's remote server over the Internet.
We can identify this in packets that have the "a" field "b.m.sys.location.get".
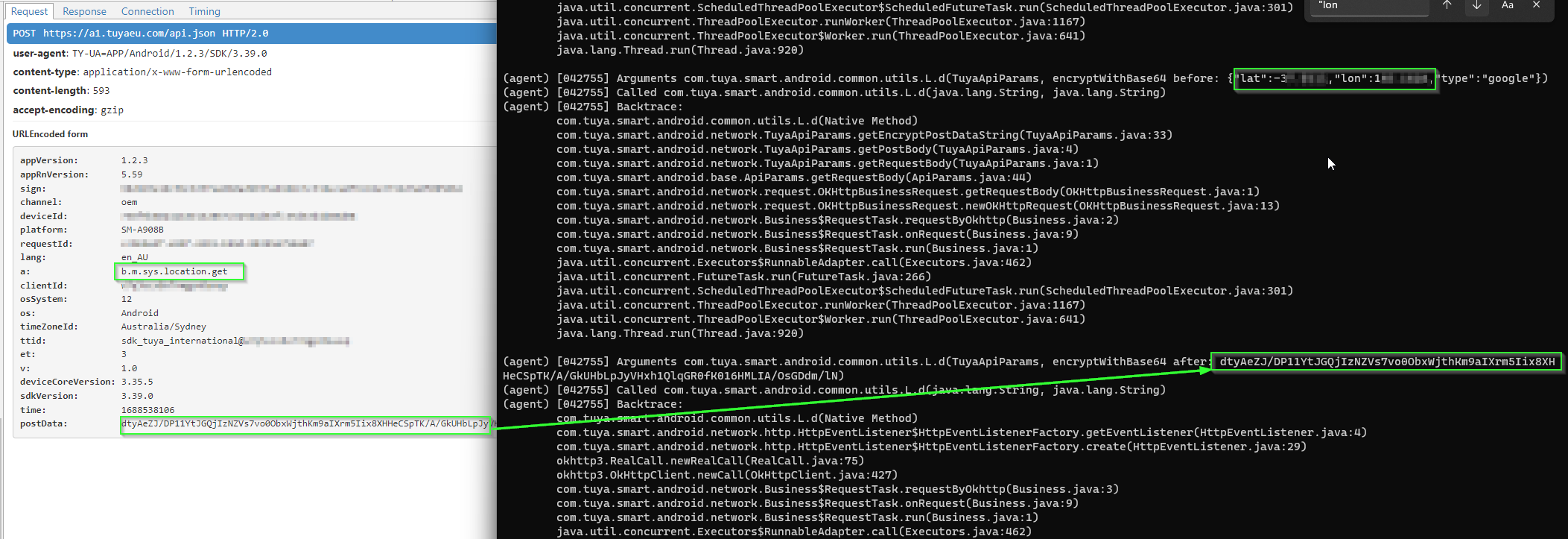
5:21 PM · Jul 5, 2023
So what do we make of all this?
The developer discloses on the app store that the precise location data collection is optional.
Is this misleading?
What we have discovered in this Twitter thread is that if you try to pair one of their devices via Bluetooth scanning, the app opportunistically siphons up your GPS co-ordinates and send them over the Internet to a remote server.
The only way to avoid this would be to manually pair the device over Wifi and avoid the Bluetooth pairing option.
Have the 500k+ people who have download Grid Connect from the Google Play store been mislead?
What do you think?
https://play.google.com/store/apps/details?id=com.arlec.gridconnect
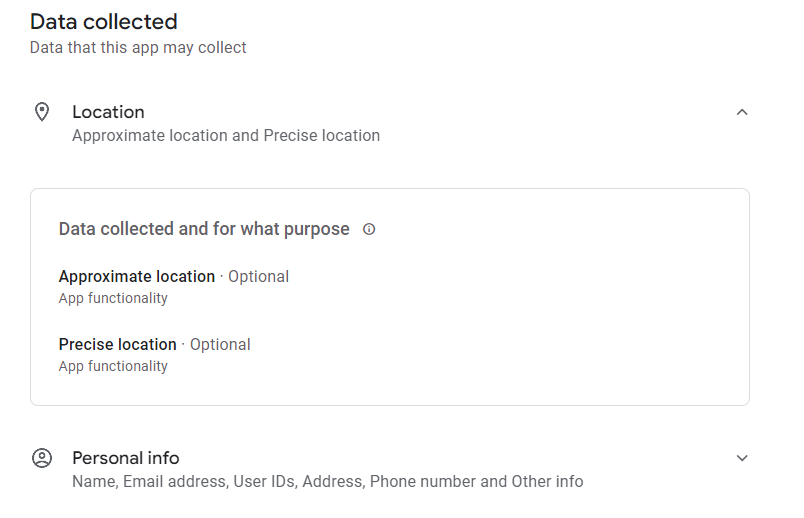
5:35 PM · Jul 5, 2023
Going to wrap up the live tweeting on this one.
If you found this interesting/helpful, feel free to like/retweet. We need as many people as we can to be encouraged to discover and call out companies that harvest location data from their devices
5:54 PM · Jul 5, 2023
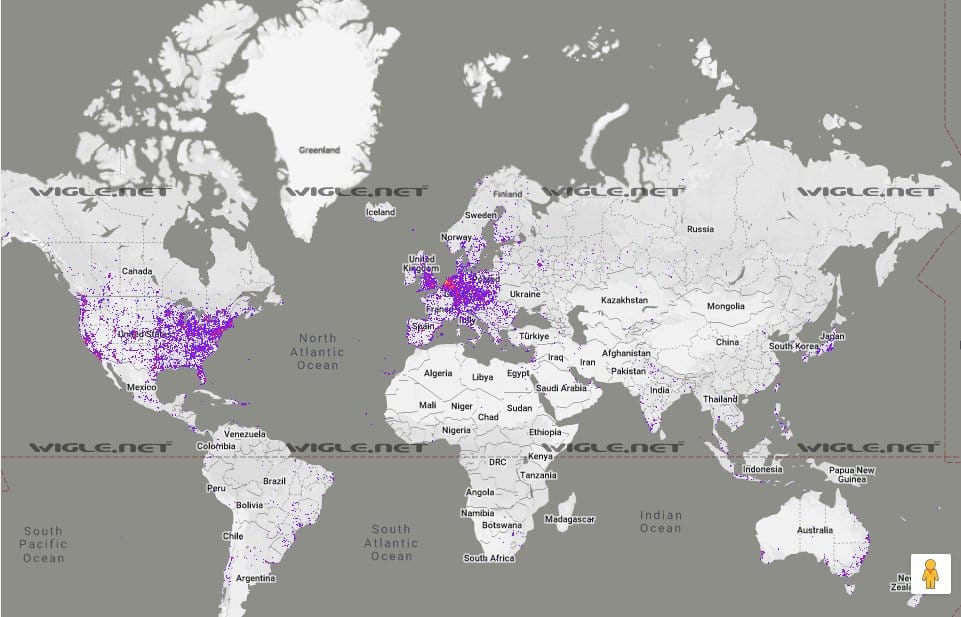
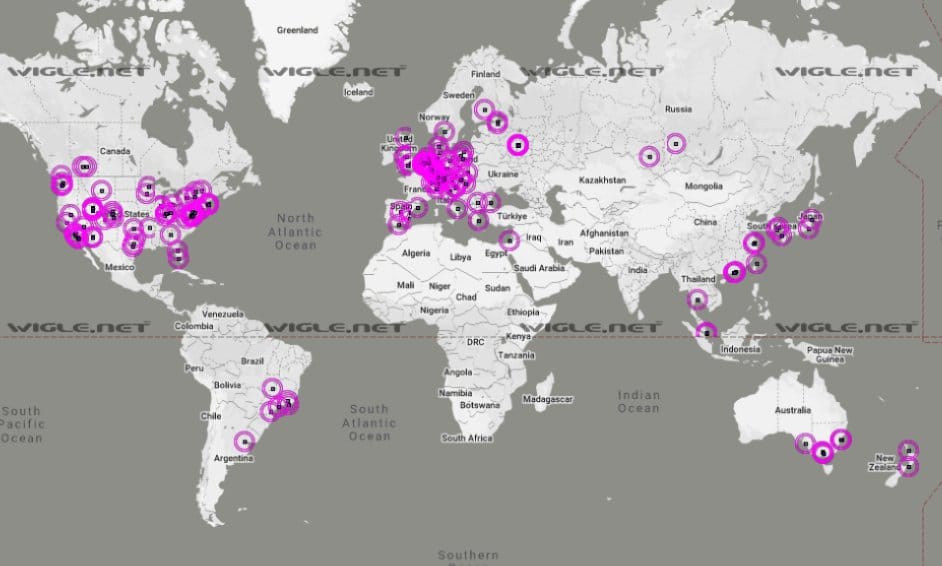
It doesn't feel complete with out a map.
Coverage map using advertised BLE device name "TY" and the mac address prefix A8:80:5 (Tuya Smart Inc.) - beaconed out from my lightbulb.
This is why Google (rightfully so) considers Bluetooth scanning "location data"